How proxies can help your privacy
Secure search of information in the Internet space and protection of user data are the main factors for users. That’s why they study in advance all the possibilities and tools that will help to increase this indicator. Of course, there are many reliable browsers, but the user should also think about how to increase the level of preservation of their confidential data.
Many users for this purpose run proxies for privacy and prevent third parties from accessing information about themselves. This is about creating special blocks that block access to your information. They will also prevent third-party organizations from getting information about your location or tracking your digital fingerprint.
Today, proxy servers have become a reliable partner for many users around the world. Let’s take a closer look at their working principles, classification, and how they can help to ensure the safety of users on the Internet.
What is a proxy
Before understanding the capabilities of this tool, it is worth understanding in general what a proxy server is. It is an additional link between the user and the Internet site he wants to visit. A normal search takes place in the contact between the user’s server and the server of the company that hosts the site. As a result, information is exchanged and the site stores certain data about the visitor.
Further representatives of the site can transfer this information to third parties. Even if they do not do this, there is a possibility that advertising organizations or fraudulent resources will try to read it. And this threatens the safety of the user.
To prevent such a moment people use proxies. This tool accepts requests from the user and transmits them directly to a remote server. After receiving a response from the remote server, the request is redirected to the site. After receiving a response from the site, it returns to the remote server, and from it goes to the one who started the request.
Roughly speaking, this tool can be called a kind of diplomat, a filter that passes all incoming and outgoing requests. In this case, the anonymity of the user and his security are ensured. Therefore, this option is liked by many people working in the Internet space. But not everyone understands the importance of its use. Some people worry that using proxy servers is illegal. But they just need to learn the purpose of proxies and realize that no legislation prohibits their use.
The purpose of proxies
Once you understand what a proxy is, you can quickly understand its main purpose. The main task of such a server will be to provide additional security for users on the Internet. Otherwise, they will be worried about their data, which can fall into third hands. If with advertisers you can only fear the abundance of unnecessary advertising, then with fraudsters everything is much worse. Therefore, experienced users among the advantages also emphasize:
- ensuring anonymity;
- bypassing censorship and blocking;
- increased security;
- optimization of network activity;
- data collection and parsing of visited sites;
- application testing and development;
- protection of personal data when connecting to Wi-Fi in public places.
Each of these items is important to users. For example, the ability to provide anonymous visits to sites will not have the consequence of additional advertising. If the selected sites are blocked in the territory of the country of residence, then with the help of proxies it will be possible to bypass this ban. For those who work over the Internet, such an advantage can be decisive.

Since proxies will filter malicious traffic, the probability of getting a DDoS attack is reduced many times, and the stability of the site and online services that are run from home is increased. For working marketers, this tool allows you to safely visit competitors’ resources and analyze their market. Developers use it to test applications. For example, to test its functioning in different parts of the globe.
As you can see, there are quite a lot of examples of successful use of proxies. They increase the privacy of users on the Internet. It remains to understand how proxies are classified and which server is best to choose in different situations.
Classification of proxies
To understand how proxies work and how they ensure the confidentiality of user data, users should study their classification. Many people are surprised that these servers are quite a lot of varieties because most of them are divided simply into paid and free. But the classification of proxies is much broader and it is important for those wishing to use such a tool to understand this. Most experienced users can categorize such tools by:
- the principle of their operation;
- type of supported protocols;
- availability;
- additional criteria.
Each of these parameters has its peculiarities and if you correctly define the purpose of using this tool, you can pick up a high-quality, safe, and reliable proxy server. Let’s analyze each variety in more detail and show it clearly.
Principle of operation
When users first study the question of what a proxy server is for, the first classification they encounter is the principle of their work. In this case, there can be 2 types of proxies: forward and reverse.
Forward proxies work linearly. They are between the user and the website from which he wants to get information. All requests are made directly through the proxy and the user will be contacted only with it. Direct tools allow you to bypass blocking sites and change IP clients.
They also provide an opportunity to run pre-caching functions on pages that are frequently visited by the user. As a result, pages will load faster. Such functions are most useful for closed networks (corporate sites or admin panels).
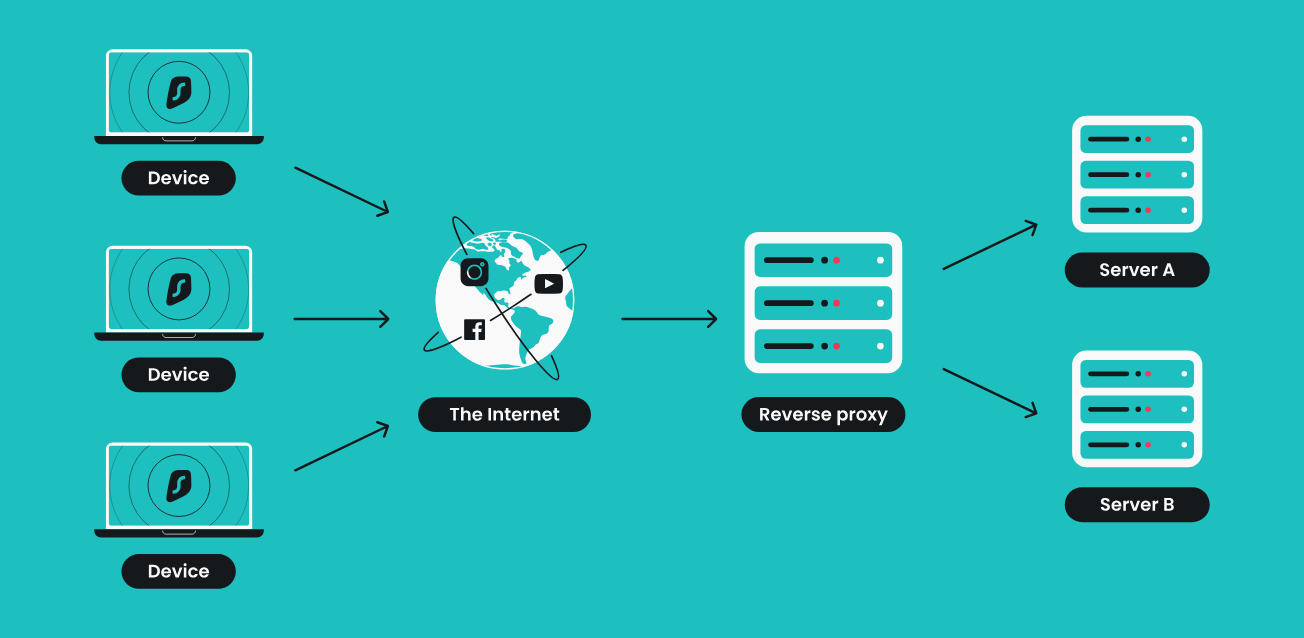
Regarding reverse proxies, the interaction here is quite different. In this case, the proxy will be an intermediary on the site side. It will process all requests and redirect them to several servers. As a result, the load on the site is evenly distributed and requests are filtered.
If suspicious activity is detected, such requests are subject to immediate blocking. Also, thanks to this tool it will hide the real address of the server. Since an additional IP address is used, users will have problems in determining it as well. As a result, the risks of server hacking and excessive spam to the site are minimized.
As you can see, these options help different target audiences. You should choose the right proxy based on which of the parties the user will represent during interaction.
Support for protocol types
Studying this option will also help users understand why they need a proxy server and how to work with it. Encryption protocols help to hide the necessary information. If you understand what protocol is used for what purposes, it is easier to determine the type of the necessary proxy. This makes the task much easier for both the user and the company that offers them such a server. All proxies are allocated based on the protocols:
- HTTP;
- SOCKS;
- Transparent;
- Residental.
HTTP proxies are used for processing of corresponding requests. They are most often used in individual proxies. In this way, users can view the pages they need faster as an anonymous user. SOCKS-based proxies work at a lower level. They are aimed at providing secure data transmission. They are also often used to bypass the restrictions of a particular network.
Transparent operates invisibly to users. They are used more for data caching. They can also be used to filter traffic. However, most users will not be able to notice the effect of this proxy. As for Residental, they work through real IP addresses with connections to home networks. Because of this, it will be very difficult to track its work and block it.
As you can see, you can find different proxy options by protocol type. The user only needs to understand what goals he will pursue when running the tool and based on this choose the right type by protocol of use.
Availability
Figuring out what a proxy is, why it is needed, and what are their differences, users should pay attention to the parameter of accessibility. Here the division is more familiar and understandable for users. According to this characteristic, they can be paid and free. It would seem, why overpay because you can take free proxies and there are a huge number of them on the Internet. However, they have several important disadvantages that users should take into account. Among such disadvantages stand out:
- instability of work;
- compromised IPs;
- higher probability of catching a virus.
The instability of work is very annoying for users who run free proxies. Since they are openly accessible, anyone can use such a tool. As a result, there is a heavy load on the IP and there is a probability that the proxy will load the page for a very long time. If you get to the moment when there are not so many visitors, this problem is not noticeable. But the lack of stability can piss off the users even more.
The problem with IP addresses should also be taken into account by users. Free proxies can be used by everyone. Accordingly, their IP cannot be updated and will be repeatedly exposed by scammers when trying to hack sites, using spam bots and other things. As a result, the IP address will already be compromised and most likely entered into the database of risky addresses and will be blocked. This negates any advantage of a free proxy server.
As for the risk of catching a virus, the problem arises because of the large number of visitors to such proxies. They can get the virus through spam bots or by visiting servers that are already infected. Some companies use free proxies for phishing purposes. In general, free tools don’t always have good protection. Therefore, if you need real reliability when working in the online space, it is worth considering reputable companies that can offer quality proxy servers to work with.
Other criteria
The previous criteria are qualifiers that all users know about. But there is a part of the features that not everyone pays attention to. But by them, it is also possible to divide such tools. Experienced users first of all divide proxies by the type of supported IP protocols.
Today there are versions of IPv4 and IPv6 protocols. The first version is older and all sites can interact with such addresses. The second type of protocol has been used more and more often recently. Many sites already allow access through the IP of this format. But using the updated version of the protocol, remember that there is a chance not to go to one of the old major web resources.
They can also be divided by individuality. Such proxies are common and private. Private ones allow you to get an IP for individual use. It will be unique and will allow only you to work through such an address. Common ones are provided for a group of clients. They are more accessible, but the cost of such addresses is much cheaper. Therefore, users should decide in advance whether they are willing to pay more for access to an individual address.
The last type can be static or dynamic IP. The former provides users with a pool of addresses. They will not change as long as the rent is paid. Dynamic proxies allow you to change IP in a certain time interval. For users who regularly visit the same sites, it is best to use dynamic options. Then it will be possible to avoid blocking your IP when visiting a resource.
As you can see, there are quite a lot of ways to classify proxies. But all of them fight for the protection of user’s data to different degrees and help them to prevent information leakage to third parties. That’s why you should think over your budget for proxies in advance, and understand your capabilities and expectations of what you will get from the use of such servers.
Advantages and disadvantages of using proxies
Understanding how a proxy server works users should understand their capabilities. Based on this, you can understand the advantages and disadvantages of using such tools in your work. In general, proxies are quite a useful option, but users should understand their functions. To the advantages of using such servers, users mainly attribute:
- the possibility to work anonymously on selected web resources;
- a chance to bypass censorship on the site;
- increased security of web surfing;
- the ability to filter incoming traffic;
- acceleration of interaction with the resource;
- the ability to properly distribute loads of incoming traffic.
Each of the advantages is aimed at different categories of users. For example, traffic distribution and web surfing may not be necessary for all users. However, anonymity and censorship bypass are the criteria that users pay attention to most often.
Of course, this tool has several disadvantages. First of all, it reduces the speed of information processing. The presence of an additional link in the chain of actions cannot allow you not to feel the loss of speed. The wait may not be so great, but if you are accustomed to instant page loading, you will have to wait a little longer.

In addition, some servers may restrict access when using proxies. It’s also important to remember that using them doesn’t always guarantee you data protection. Although the chance of hacking is reduced over time, phishing programs are also developing daily because of their stable popularity among advertisers and site hackers. So periodically data may fall into the hands of advertising companies, but reliable proxies quickly find ways to counteract innovations in the online space.
Conclusion
Among all the available tools to protect data on the Internet, most of them use VPN services. But this tool rather protects information at a basic level and will not be able to provide the proper level of protection for user data. Also, it is more of an option to bypass blocking.
A proxy server will help encrypt your data. This ensures that the user information is more secure. Therefore, the use of proxy servers is more interesting for experienced users, who for work or other purposes have to visit different format sites.
To understand what a proxy does, users should first of all understand why they will use this tool. With its help, it is possible to achieve greater security for user information. And this is the main reason for using proxy servers.
In general, it is quite an interesting way to bypass blockages and work with websites. Users don’t have to worry about their data falling into the hands of advertisers, or even worse, scammers. Many of the options available level out the tracking capabilities of digital footprints. This means that the history of your visits will be inaccessible to categories of users who want to use such data for their purposes.
Today, you can find quite a large number of different proxy options on the Internet. Analyze each available option according to our classification, and you will understand which of the tools is the most suitable for your requirements.
Read also
The safest browsers for iPhone
User security is an important criterion when choosing a browser for searching the Internet. Many users try to find the...
The safest browsers for Android
Most users access the Internet for recreation or to view various content. However, the majority of users use it for...
What is the difference between IPv4 and IPv6?
You can find a lot of information in the Internet space about what IP protocols are used for data exchange....
How to find out the Wi-Fi password on your phone
It is important for users to quickly find the Wi-Fi password on their phone. Thanks to this, they connect to...