Proxy servers – available solutions and their features
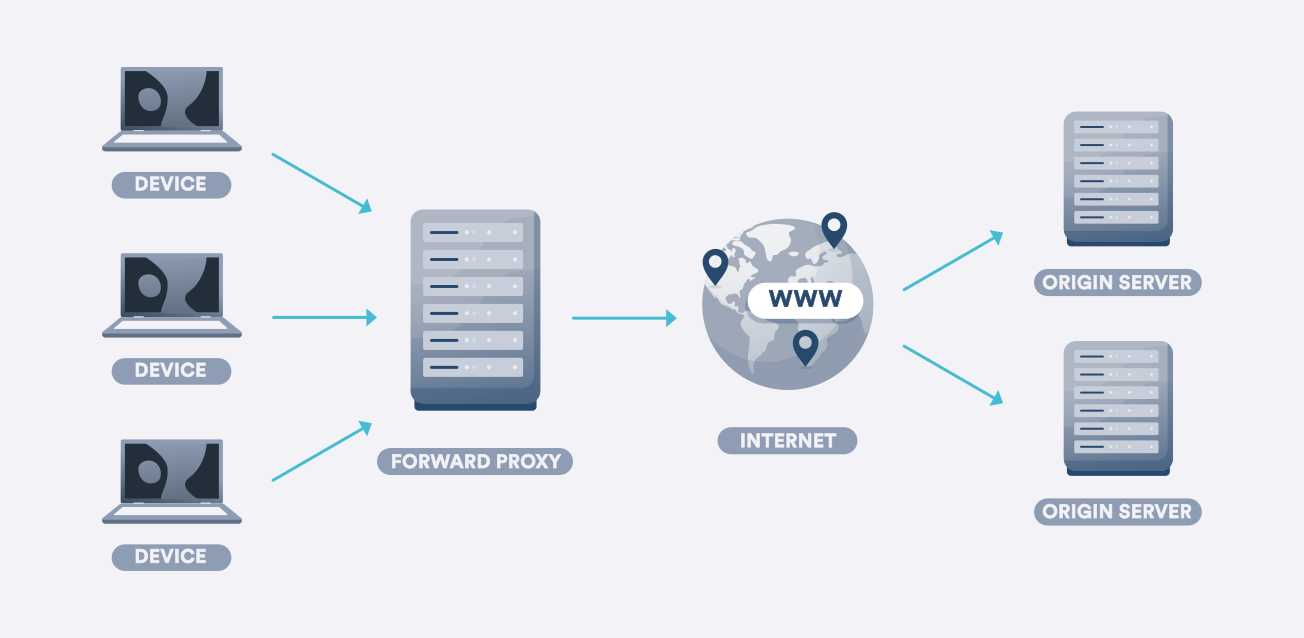
Proxy servers are extremely important for monitoring Internet traffic, ensuring the anonymity (security) of users. There are various types available today, each providing unique functionality and designed to meet specific needs. Understanding their features and specific use allows you to easily select the most suitable option for your specific needs.
Main types of proxy servers
Proxies are classified according to different criteria that determine their functionality and use in different scenarios. Here are just a few of them:
- Anonymous proxies do not transmit your IP address to sites, providing a higher degree of anonymity.
- Transparent proxies do not hide the IP address, but are able to cache content to speed up loading.
- SOCKS proxies are suitable for applications that use different protocols besides HTTP, for example for P2P networks.
- Residential proxies – use the IP addresses of ordinary Internet users, which makes them less susceptible to blocking.
- Distorting proxies – transmit the wrong IP address, creating the illusion of being in a different location.
- Dedicated proxies – provide private IP addresses that are used by one user, providing a high level of confidentiality.
How to choose the right type of proxy for your needs
Selecting the right proxy depends on the real needs and tasks facing the user. If anonymity and security when surfing the Internet are important, then the best options would be anonymous or dedicated proxies. For companies working with large volumes of data, residential or SOCKS proxies are extremely relevant, providing greater opportunities for interaction with different protocols and minimizing the risks of blocking. It is also important to consider the cost and level of support provided by the provider, calculating the estimate based on your available budget.
Proxy servers are a powerful tool for online security and anonymity. When choosing a proxy, it is important to pay attention to its type and the specifics of the upcoming use, functional aspects and estimated costs. The right choice from a trusted service provider will allow you to solve any problems as efficiently as possible, be it secure access to resources or bypassing geographical restrictions.