How to encrypt your WiFi connection on your phone
Today, Wi-Fi networks are used both in private homes and in various business structures. For users to safely use them for their purposes, it is important to apply some security parameters. Otherwise, data about users can become available to other users in the Internet space. And we are not just talking about names or phone numbers but about confidential information including account numbers.
To prevent this, it is important to use encrypted connections. However, not all users understand how to encrypt WiFi and continue to use their usual connections. This article contains some of the most popular options for encrypting data. Some do not require special efforts but are quite effective against fraudulent actions. Let’s analyze each of them in as much detail as possible.
Reasons for encrypting Wi-Fi connections
Thanks to special encryption algorithms, some kind of boundaries of protection of your gadgets are established. These algorithms are used both on websites and applications. Since internet connections are considered vulnerable, it is best to improve their protection or your data could be accessed by third parties. Some of the most commonly stolen data include:
- personal passwords;
- bank card information;
- current account information.
The owner of such information can simply take possession of your finances and it will be almost impossible to get them back. Therefore, it is best to understand in advance how to encrypt your Internet connection and do it as quickly as possible.
Encrypting your information does not guarantee your safety on the internet. However, the chance of being hacked and losing confidential information will be noticeably lower. By encrypting Wi-Fi connections, you can scramble the information you send and the data you receive. Thus it will be unreadable for all users, except those who have the necessary key for decryption. This is a noticeable increase in your security. Let’s take a closer look at the most popular ways of encrypting Wi-Fi connection data.
Popular Wi-Fi encryption options
Typing the phrase how to encrypt my Internet connection into a search engine, a user can find dozens of different options. An inexperienced user will immediately try to run the simplest of the options. But more experienced will check them, read, and study the necessary information. These actions are no less important elements of protection.
Unfortunately, some scammers may advertise certain encryption methods so that users use them. But the problem is that such methods are more likely to have the opposite effect and by using one of the options users simply open their data to third parties. Among the safe and convenient ways of Wi-Fi encryption the most common are:
- using popular protocols for data encryption;
- checking router settings;
- changing the network name regularly;
- changing the network password regularly;
- using a guest network;
- using proxy servers.
Each of these methods has its advantages and disadvantages. But in general, they all help to protect your gadget from possible hacking. All that remains is to understand which option is best for you and use it to protect your personal information.
Learn the basic data encryption protocols
Before analyzing the methods of decrypting traffic, users should understand the basic processes in advance. Encrypted data can only be read by someone who has the necessary key. Therefore, various options for data encryption protocols are created. Experts cite the following protocol options as the most popular options for encryption:
- Wired Equivalent Privacy;
- Wi-Fi Protected Access;
- Wi-Fi Protected Access II.
When searching for the right protocol, it is important to realize that each of them can provide security at different levels. The weakest of the above protocols is considered to be WEP. It was one of the first protocol options, but in the current environment, it is not recommended to use it. The other protocols are more advanced and can provide security at a serious level.
The Layer 2 protocol is considered an enhanced version of Wi-Fi Protected Access. It is most often used by users together with a dynamic encryption key. Due to the constant change of IP address, it is much more difficult to crack it. Therefore, this encryption protocol is considered a priority in use and when choosing encryption methods a user should first pay attention to it.
Checking router settings
To encrypt web traffic, users need to check the settings of their router. Since they are initially set by default, it is best to change all passwords, security settings, and encryption. Usually, the basic settings are not the strongest. Therefore, with a more or less competent approach, it will not be difficult to hack them.
To ensure adequate protection, it is best to go into the router settings. To do this, you only need to type the current IP address in the browser and log in. After entering the login and password, you can start the administration process. By setting up all the processes correctly, users will be able to improve the security of their router and prevent fraudsters from hacking into their home network.
The procedure will not take a lot of time. If you are worried or need advice, you can either contact your loved ones who are better versed in the matter or specialized companies that you trust. Once all processes are completed, you will only need to save and restart the router. For a knowledgeable person, the process will take no more than 10 minutes. But they are worth spending to increase the security of your sensitive data in the Internet space.
Changing network names
Quite simply at first glance how to encrypt Internet traffic without a VPN is considered to change the name of the network. It is quite easy to do. It seems that changing the name of the connection will not help, but this is not the case. With such a change, you can confuse a hacker who is unaware of the name change. After a few failures, he may give up trying to get your data and switch to easier “victims”. Hacking can be prepared for a particular model or type of router. And if you change the name to a completely different variant, the hack will fail. To change it, you need to:
- go to the administration panel;
- find the default network name (or SSID);
- change the name and save.
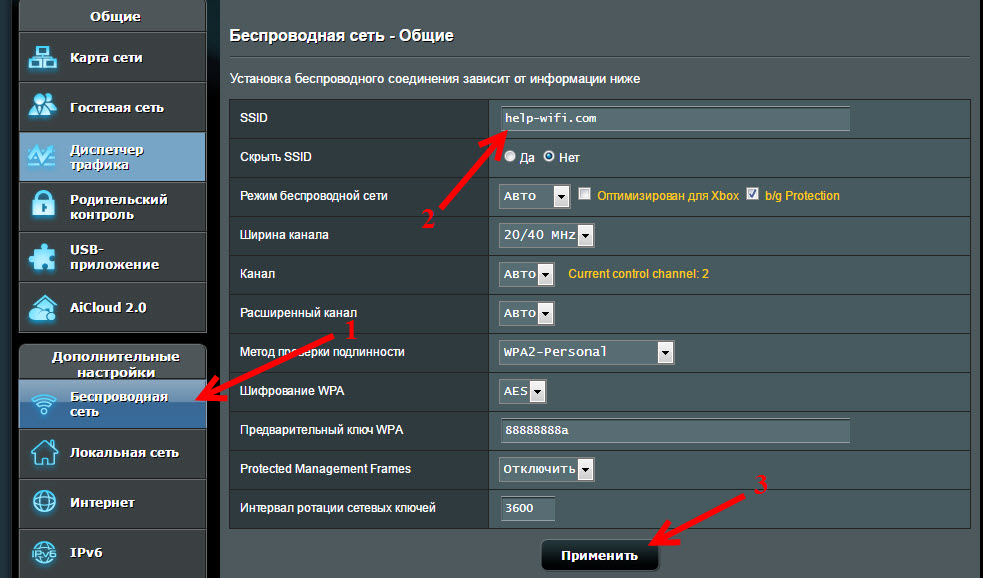
When making these changes, it is important not to enter personal information. In this case, any changes can only make your situation worse. But if done competently, the likelihood of your network being hacked will be much lower. Of course, this does not guarantee the complete security of your connections, but with these changes, the security of your information will be higher. And this is the goal that most users pursue when encrypting Wi-Fi.
Changing network passwords
As we have already realized, encrypted network traffic is more secure for users. That’s why it’s best to change the default password on Wi-Fi in addition to the name. They are available to users, many are created by specific ciphers and given by random number generators. Therefore, for an experienced hacker to crack them will not be very difficult. Changing your password regularly will help improve the security of your data. Experienced users recommend that when creating a password:
- use password generators and change them regularly;
- Use uppercase and lowercase letters in the password combination;
- add numbers to them;
- use special characters;
- the minimum password length should be 10 characters.
Such actions are extremely important for user security. You should not put on the router the same password that you had at your previous place of residence or use it in your usual accounts (e.g. e-mail or social network pages). You should also avoid using familiar combinations of popular characters or numeric sequences. It is not recommended to use publicly available memorable dates in the life of users. In this case, you will weaken the protection of your connections.
Guest networking
Another interesting option to encrypt network traffic from Wi-Fi is to set up guest networks. This way you will have a separate network for you and your family and no outsiders will have access to it. This step is often used in offices or public places (cafes, restaurants, shopping malls). But no one forbids you to create an analog at home.
If you know how to configure the network, then creating another one will not be difficult. In the guest network, you can not just protect yourself from other users. You will also manage bandwidth and can restrict access to unknown devices or third parties. And this will greatly improve the security of your internet connections. To get data from your network it will need to be hacked. If you use other methods to encrypt your data, the chances of hackers succeeding will not be the highest.
Using proxy servers
This method is one of the most popular options to encrypt all network traffic from your gadget. It is utilized regularly because of its many features and advantages. A proxy server acts as an intermediary. As a result, it redirects your requests and you get well-encrypted WiFi traffic. Some of the big advantages of this method include:
- speed of data processing;
- flexibility in operation;
- high degree of protection;
- absence of the usual inaccuracies compared to other options;
- ease of operation.
The main advantage of proxies is their data processing speed. It is much higher than that of VPN connections. This is possible due to the connection of independent processes in the nodes between the target request and proxying. The latency of data transfer is leveled out due to this autonomy.
Unlike other options, proxy exposure can be limited to specific applications and this flexibility is not available with all options. If you are using such servers via a PC, it is possible to not extend their impact to specific domains. Also, the work of proxy servers is very difficult to detect. You need to perform additional configuration and individual servers can give information for the work of HTTPS connections. Conditional VPN will be noticeable even for primitive programs.
Unlike other encryption options, the proxy will not be interrupted. Also, the system does not require a high-functioning smartphone for installation. Therefore, these servers are worth using in work. You can configure them by the following steps:
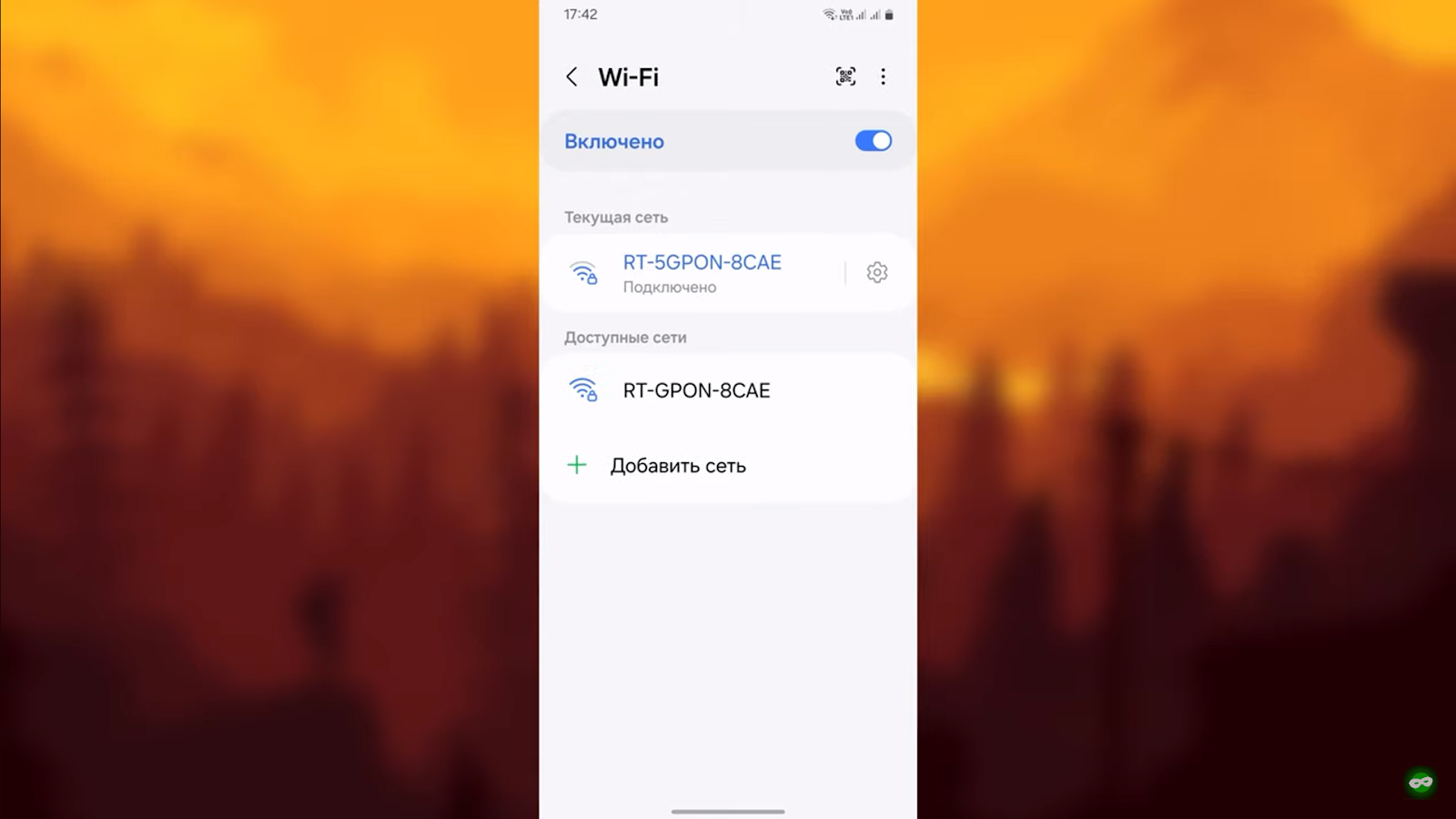
Open the settings on the smartphone and specify Wi-FI
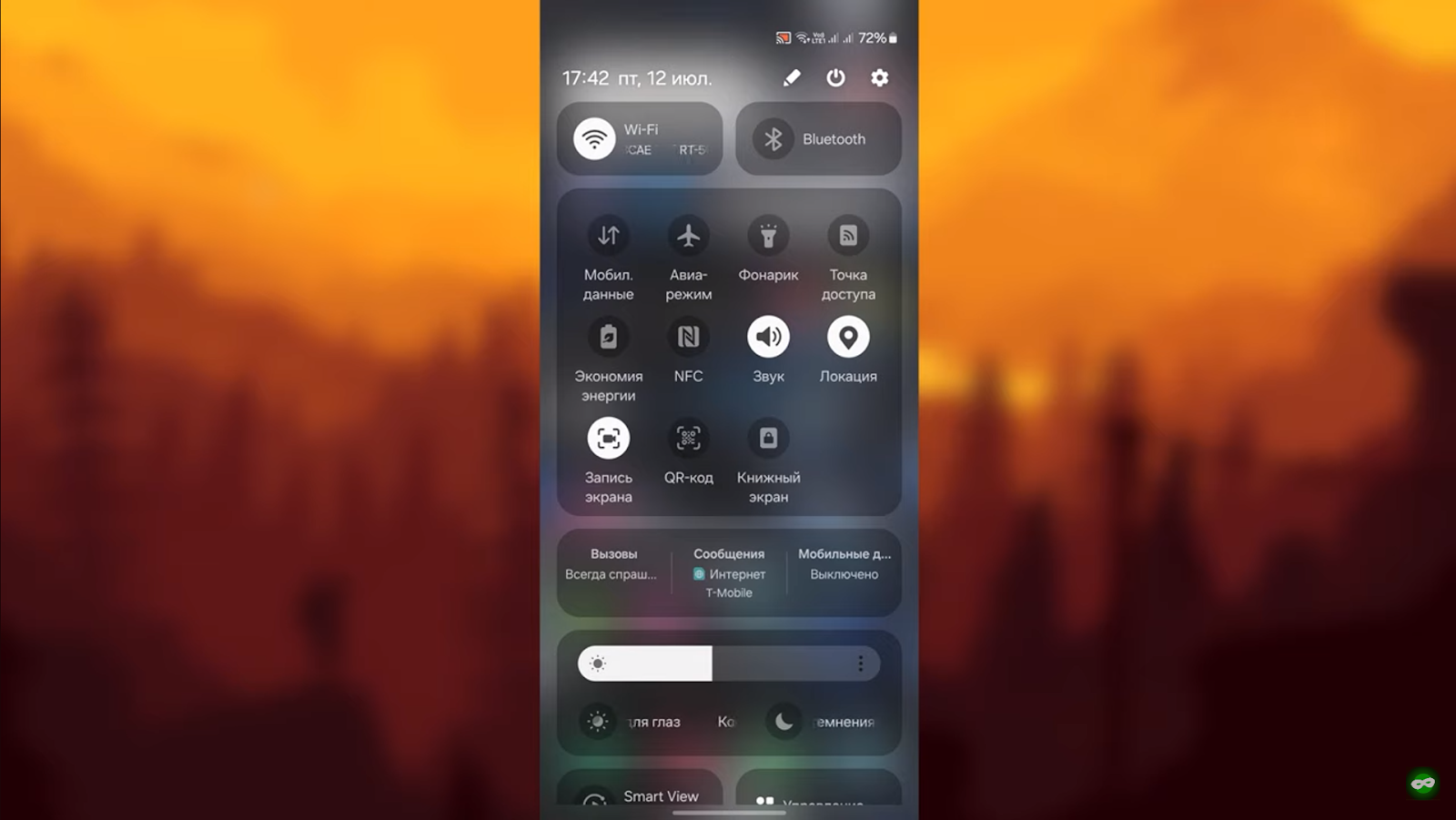
Specify the current connection and click on the arrow (or circle) on the right side of the screen
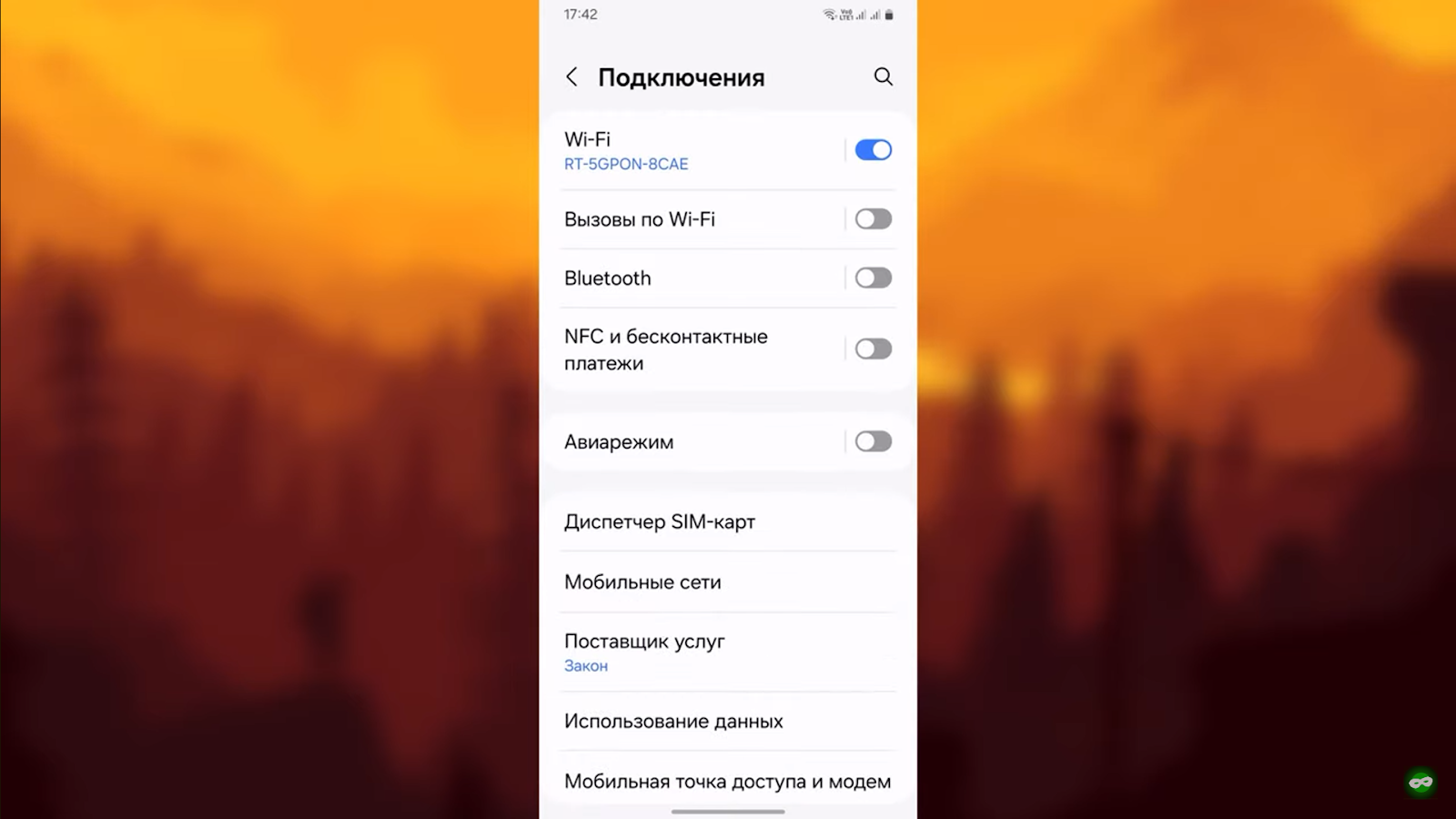
Select the Proxy option and specify “Manual” instead of “No”.
In the new menu, fill in the hostname, and port, and specify exclusion sites.
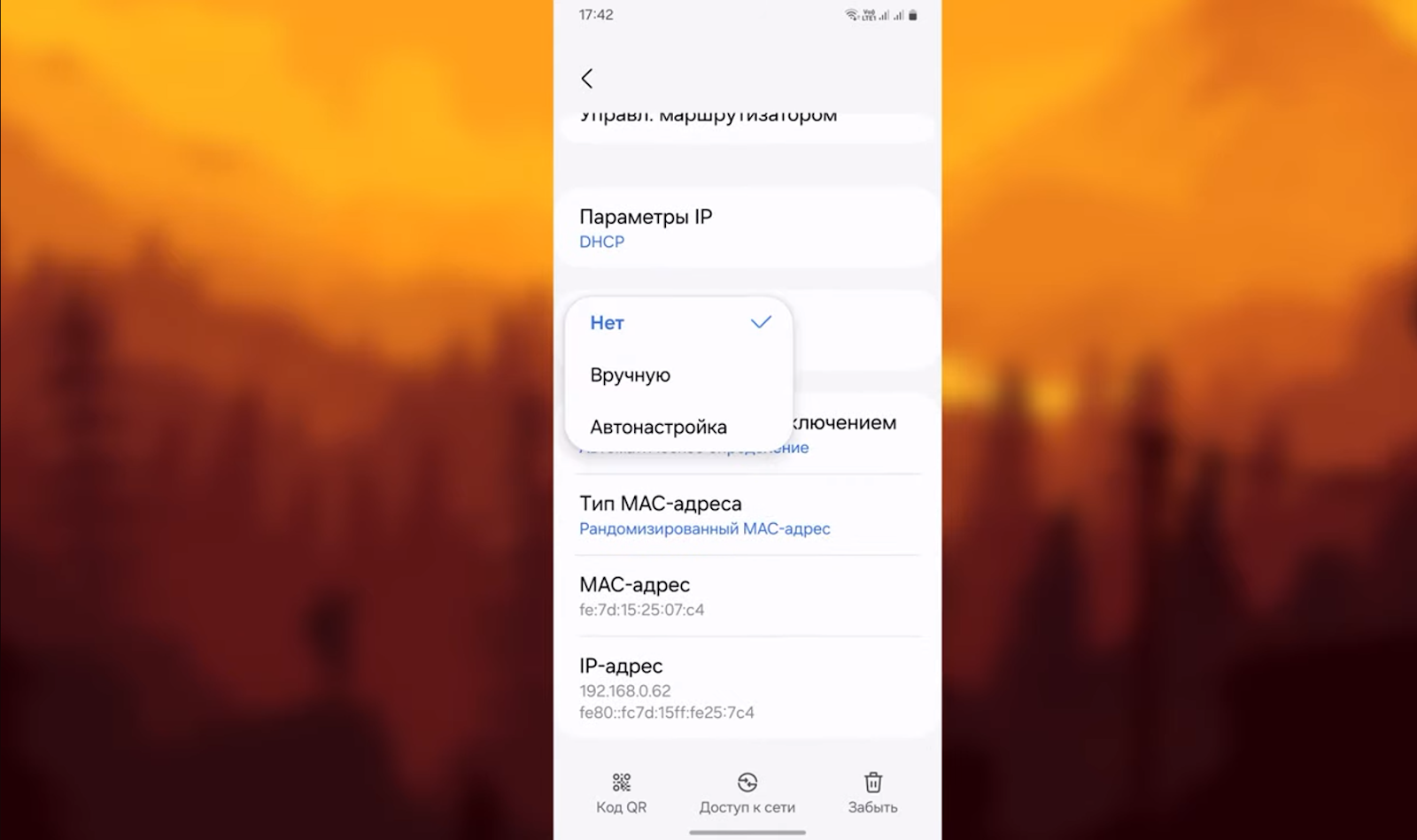
Save the entered data and pass authorization for private proxies.
After that, you can run a customized proxy server and not worry about the encryption level of your Wi-Fi connection.
Conclusion
As you can see, there are plenty of options on how to encrypt a Wi-Fi connection. The user only needs to choose the most suitable one for him and take advantage of such a step. If this is not done, the security of his connections can be violated. In turn, this can lead to unexpected trouble for the user. Therefore, it is worth using at least one of the options we have mentioned for data encryption.
Read also
How proxies can help your privacy
Secure search of information in the Internet space and protection of user data are the main factors for users. That's...
The safest browsers for iPhone
User security is an important criterion when choosing a browser for searching the Internet. Many users try to find the...
The safest browsers for Android
Most users access the Internet for recreation or to view various content. However, the majority of users use it for...
What is the difference between IPv4 and IPv6?
You can find a lot of information in the Internet space about what IP protocols are used for data exchange....